 Diagram A.
Diagram A.
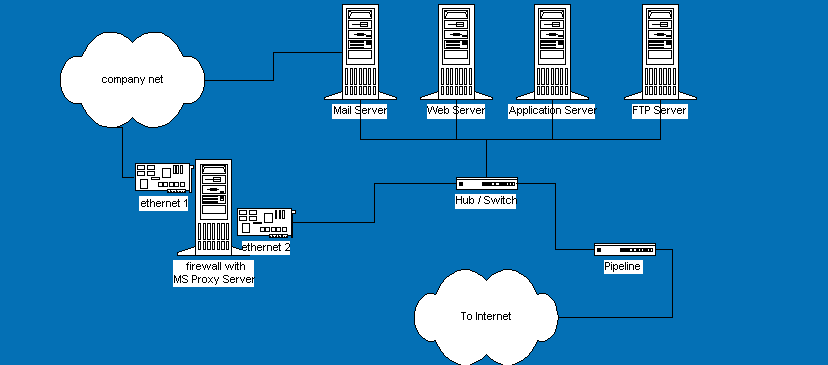
What is a Firewall?
The word firewall is just a term used to describe an interface that blocks or prevents access. This is both at the physical layer, virtual network layer (protocol), and application layer. A firewall is a special device running software that allows or denies access to its resources. A true firewall will not let any two networks talk to each other without special software. This special software could be firewall management applications, proxy servers, or built in firmware.
A TRUE Firewall
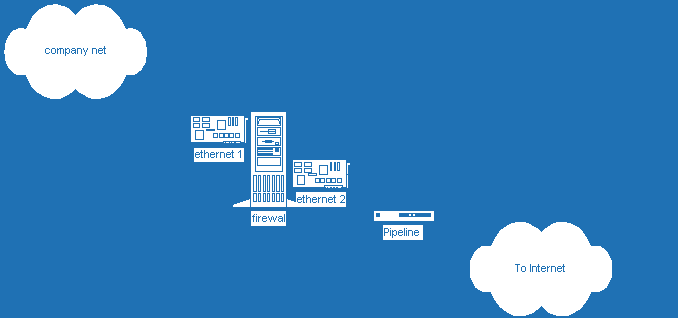
Diagram A shows a true firewall.
- this is a firewall on the physical layer because of 2 different hardware cards
- this is a firewall on the network layer (protocol) because there is no routing between networks
- this is a firewall on the application layer because the protocol that the application might use is not routed
 Diagram A.
Diagram A.
The physical layer can always be achieved by having 2 separate Network Interface Cards (NICs). Special attention is always given to the protocol layer since here is where the majority of espionage takes place. NetBEUI, IP, and IPX are the main communication protocols that are implemented within today’s applications as well as today’s networks. IPX is usually Novell specific and NetBEUI is not routable across WANs. IP is the defacto standard for application communication. Telnet, mail (smtp & pop3), ftp, tftp, nfs, www, and nis are the most widely used applications that have the most security threats.
Diagram B. shows that any interaction on the application level from within the company network halts at the firewall. This is because there is no protocol routing or proxy server. Likewise, anyone trying to get in the company network from the Internet will be stopped. The latter is the ideal solution for most companies – denying access from anyone on the Internet to critical company resources. But both diagram A and B deny access to the Internet from within the company net. A proxy server can control the access to and from the Internet on an application level.
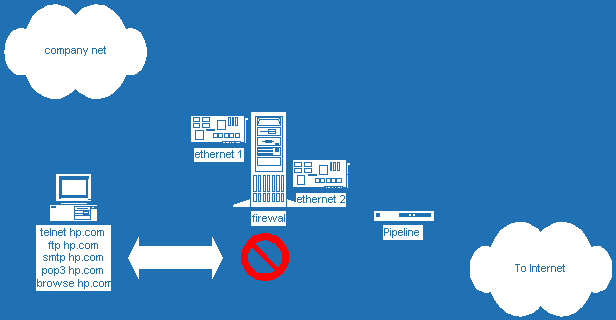
Diagram B.
Proxy Server on the Firewall
Microsoft Proxy Server creates a single, secure gateway to the Internet. In addition, its active and intelligent caching capabilities store frequently accessed data. MS Proxy Server works with IP and IPX. Network applications like smtp, pop3, ftp, and www are proxied then routed to the Internet and back. Special rules allow access from specific ports or addresses. Diagram C shows the Proxy in action.
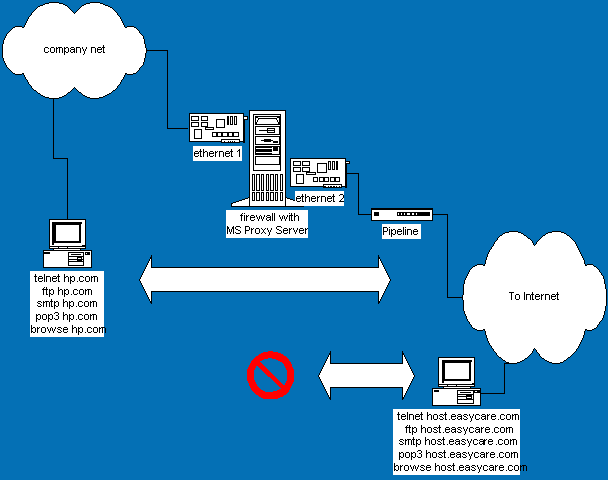
Diagram C.
What Happens to ECOM with a Proxy Server
The MS Proxy Server denies access to specific network applications. But access can’t be denied on the company mail server or the company web server. So, the servers would be moved to the Internet side of the firewall. The firewall is forcing the division of machines into two networks and therefore dividing resources.
A new network Hub or Switch is necessary to support the new network on the Internet side of the firewall. Special consideration should be given for future uses of the new LAN.